Networking
R&S / DNS
Switching;
- To make two computers/VMs reach each other, we connect them to a switch which will create a network containing the two systems.
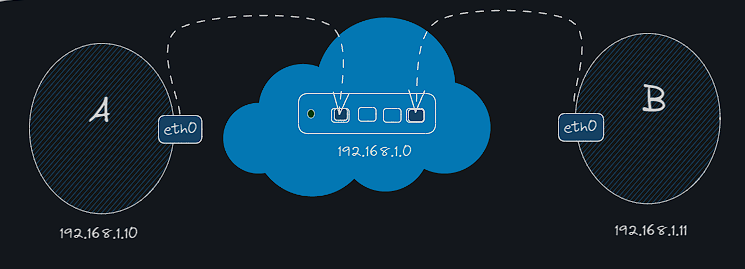
- to see interfaces with your host use →
ip link
- To assign an IP address to the system use →
ip addr add 192.168.1.10/24 dev eth0
Routing;
- To connect two networks we use a router. The router acts as a gateway to the world which is the internet.
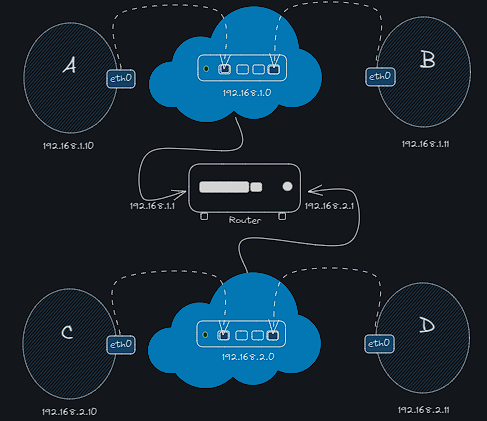
- To let the systems aware of the gateway we configure the route table →
ip route add 192.168.1.0/24 via 192.168.2.1
- to check the routing table →
route
- to configure the default gateway →
ip route add default via 192.168.2.1
IP Forward;
- By default, Packet forwarding from one interface to another is disabled for security reasons.
- To allow IP forwarding we add the following line
net.ipv4.ip_forward=1to /etc/sysctl.conf.
sysctl -ato verify andsysctl --systemto reload sysctl config.
DNS;
- DNS is your phonebook to the internet. It assigns a name to an IP address so every time you connect to that IP address you don’t have to write it, Instead, you specify the name of that IP.
/etc/hosts→ to translate a hostname to IP addr.
/etc/resolv.conf→ to specify your DNS server.nameserver <ip>
/etc/nsswitch.conf→ to change the DNS resolution order.
- To make two computers/VMs reach each other, we connect them to a switch which will create a network containing the two systems.
Network Namespaces
ip netns add <name>→ to create new namespace.
ip netns exec <name> <cmd> | ip -n <name> <cmd>→ to exec a command within the created network namespace.
ip link add <ns_inf1> type veth peer name <ns_inf2>→ to connect two ns together using a virtual cable.
ip link set <ns_inf1> netns <ns_name>→ to attach an interface to its appropriate ns.
ip -n <ns_name> link set <ns_inf1> up→ to bing the interface up.
How Container Networking Works - Building a Linux Bridge Network From Scratch | iximiuz LabsBegin with the basics to understand Docker and Kubernetes networking: learn how to create and interconnect network namespaces using standard Linux tools.https://labs.iximiuz.com/tutorials/container-networking-from-scratch/

Pod Networking
- Networking Model;
- Kubernetes expects every POD to get its own unique IP address.
- Every POD should be able to communicate with every other POD within the same node using that IP address.
- Every POD should be able to communicate with every other POD on other nodes as well using the same IP address.
- Networking Model;
CNI in Kubernetes
- CNI defines the responsibilities of container runtime.
ADD) # Create VETH pair # Attach VETH pair # Assign IP address # Bring Up Interface ip -n <ns> link set .. DEL) # Delete veth pair ip link del .....- The CNI plugin must be invoked by the component responsible for creating the container which is the Kubelet service.
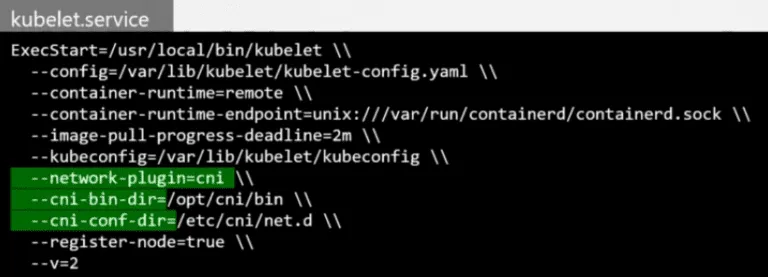
$ ls /etc/cni/net.d 10-bridge.conf $ cat /etc/cni/net.d/10-bridge.conf { "cniVersion": "0.2.0", "name": "mynet", "type": "bridge", "bridge": "cni0", "isGateway": true, #defines whether the bridge network interface should get an IP assigned or act as a gw. "ipMasq": true, #defines if a NAT rule should be added for IP masquerading "ipam": { #ipaddr management config "type": "host-local", #defines that IP addrs are maanged locally. this can be set to an external DHCP server. "subnet": "10.22.0.0/16", "routes": [ { "dst": "0.0.0.0/0" } ] } }
Ingress in Kubernetes
- Ingress is a single entry point into the cluster, that you can configure to route to different services within your cluster based on the URL path, and SSL termination. Basically a Layer 7 Load Balancer managed within the cluster.
- Ingress Controller;
- Aside from load balancing, the ingress controller has additional intelligence built into it to monitor the Kubernetes cluster for new definitions or ingress resources and configure the nginx server accordingly.
- The ingress controller requires a NodePort service to be exposed at a node port on the cluster. Also it requires a LB service to be exposed as a public IP.
- Deploying IC;
apiVersion: extensions/v1beta1 kind: Deployment metadata: name: ingress-controller spec: replicas: 1 selector: mathcLabels: labels: name: nginx-ingress spec: serviceAccountName: ingress-serviceaccount containers: - name: nginx-ingress-controller image: >- quay.io/kubernetes-ingress-controller/nginx-ingress-controller:0.21.0 args: - /nginx-ingress-controller - '--configmap=$(POD_NAMESPACE)/nginx-configuration' env: - name: POD_NAME valureFrom: fieldRef: fieldPath: metadata.name - name: POD_NAMESPACE valueFrom: fieldRef: fieldPath: metadata.namespace ports: - name: http containerPort: 80 - name: https containerPort: 443apiVersion: v1 kind: Service metadata: name: nginx-ingress spec: type: NodePort ports: - port: 80 targetPort: 80 protocol: TCP name: http - port: 443 targetPort: 443 protocol: TCP name: https selector: name: nginx-ingress
- Ingress Ressources;
- An ingress resource is a set of rules and configurations applied to the ingress controller. Rules to say simply forward all incoming traffic to a single application or route traffic to different applications based on the URL.
- Ingress to route all traffic to a backend service;
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: ingress-wear spec: backend: serviceName: wear-service servicePort: 80
- Path based routing;
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: ingress-wear spec: rules: - http: paths: - path: /wear pathType: Prefix backend: service: name: wear-service port: number: 80 - path: /watch pathType: Prefix backend: service: name: watch-service port: number: 80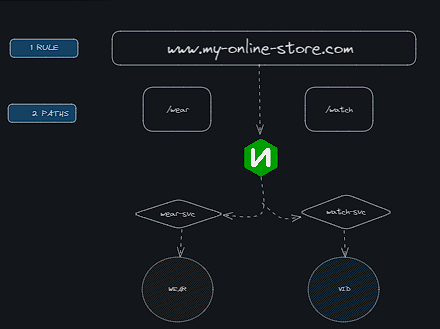
If none of the rules match, then the user will be redir to the default backend service.
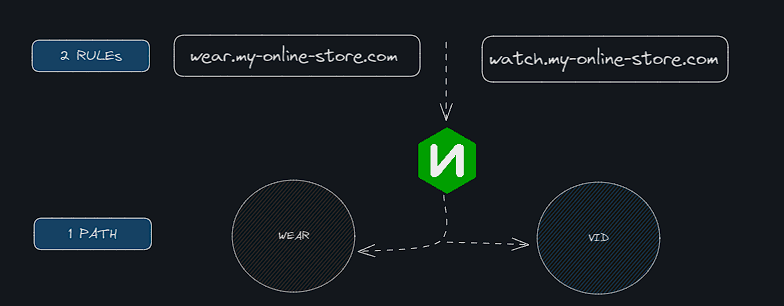
- Hostname Based routing;
apiVersion: networking.k8s.io/v1 kind: Ingress metadata: name: ingress-wear spec: rules: - host: wear.my-online-store.com http: paths: - backend: service: name: wear-service port: number: 80 - host: watch.my-online-store.com http: paths: - backend: service: name: wear-service port: number: 80